An Article by

Frank D B.
A Consultant from Duesseldorf, Germany
Search Expertbase
Hire Frank D
Virtually
Hybrid
In-Person
Collaborate Today And Compete Tomorrow?
50 Claps
2100 Words
11 min
Chances and risks of managing Key Knowledge In Inter-Organisational Alliances Or Networks in an global context.
When aircraft manufacturer Airbus signed a cooperation deal recently with a visiting Chinese delegation headed by Prime Minister Wen Jiabao commentators were somewhat suspicious. China, which is recognised as being highly successful in acquiring the technologies it lacks, has imposed clear rules: penetration of its market depends on investment that is likely to develop the Chinese aerospace industry. In this context, then Airbus President and CEO Gustav Humbert said that technology transfer will be necessary to achieve industrial cooperation. "The question is, how much of the latest technology are you able to transfer?" he said. "You have to make sure that you are the master of the newest technology and not give away technology which might work against you tomorrow, with competitors copying you later."
The growing popularity of inter-organisational alliances and networks, combined with the economic obligation to deliver knowledge leadership, has accelerated the need for firms to cooperate across geographical and legal boundaries. Nevertheless, cooperative-cum-competitive businesses may experience deviation between intended and actual knowledge flows. Parties may - deliberately or unconsciously - have different perspectives on the direction and boundaries of the knowledge component in their exchange relationship. Despite well crafted contracts and procedures, firms or organisations can use the acquired knowledge in adjacent business opportunities beyond their initial agreement.
The Delegations of German Industry & Commerce in China warns that there are joint venture partners who open their own factory right next door. Ready access to individual member's knowledge repositories affords greater scope for absorbing knowledge beyond the boundaries of any prior agreements. Alternatively, partners may try to pull tacit knowledge on top of the explicit knowledge that was specified in a contract or mutual agreement. Conflicts may arise between product delivery contracts and technology transfer agreements. Hence, on the one hand a considerable amount of knowledge has to be provided to support project realisation, but on the other hand key know-how and technologies have to be protected. Understanding these risks is important either to avoid undesirable distribution of valuable knowledge or actively to support the necessary exchange of know-how and expertise in joint business activities.
A systematic and holistic approach is needed
Many organisational alliances and collaborative projects involving the transfer of know-how or technology primarily rely on formal legal contracts and policies, which describe encapsulated knowledge assets to be exchanged as well as related procedural criteria. But, as organisations or project partners engage in a fluidly evolving and sometimes invisible exchange process, they need adjustable and flexible control strategies, which are embedded in relational contracts that broadly outline areas of exchange and codes of conduct. To accomplish this, transparency has to be ensured with respect to all the codified as well as all the tacit assets at stake, with due regard for the degree of collaboration reigning at the time.
For example, the more interconnected a multi-stakeholder delivery project is, and the more inherent knowledge imbalances exist, the higher the risk of potential knowledge misuse or loss. To understand fully the nature of knowledge transfer, one has to take into account the issue of content and context. First, the level of abstraction also determines the cost of codification, thus the more complex the knowledge is, the higher the costs of its disembodiment will be, and some forms of know-how can't even be separated from their human carrier. Second, knowledge is context sensitive. Thus, if knowledge is separated from its human carrier, e.g. during codification, a part of it is lost.
Identification and assessment of relevant knowledge assets
A focused knowledge audit should be carried out to identify, assess and categorise relevant codified as well as "human contained" knowledge resources, e.g. using structured interviews, surveys and social network analysis. The assessment follows the dimensions of competitive relevance and non-imitation potential. The first aspect estimates a knowledge object's distinctive features and related business value, whereas the second dimension characterises its complexity and thus its reproducibility.
As depicted in Figure 1, of the resulting spectrum of knowledge assets three areas are of special interest. Category A includes resources representing key knowledge, incorporating sustainable competitive advantages, the loss of which would significantly harm an organisation's business capability. Category B contains important know-how, whose business relevance has to be investigated focusing on the given situation and context. The scope and consequences of a potential knowledge transfer or loss have to be evaluated, e.g. what financial value or extent of technological leadership is at risk. Category C describes the basic know-how or common knowledge available on the market, which offers no major distinctions from competitors.
Figure 1: Knowledge analysis and assessment matrix
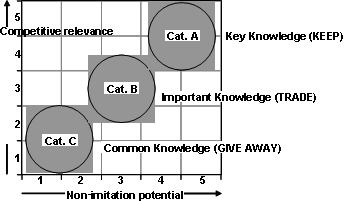
Based on these categories clear knowledge retention and protection policies can be developed e.g. using a matrix indicating the knowledge category, the proposed receiver, for example foreign company subsidiaries, joint ventures or cooperative partners as well as the related procedural rule, thus "Transfer", "Evaluate & Decide" and "No transfer".
Tacitness as a knowledge protection lever
In the attempt to enable or optimise the transfer of knowledge, the dilemma arises from capabilities that can be easily communicated within the organisation and that are more likely to be easily imitated by competitors. In contrast, tacit knowledge is more difficult to transmit, particularly if transmission is between organisations, and its effective application might be quite challenging if the receiver lacks the necessary contextual framework. Research done by Mark V. Cannice and Roger Chen, both University of San Francisco, as well as by John D. Daniels from the University of Miami, shows that organisations can decrease the chance of appropriation by raising their knowledge tacitness along two dimensions: by reducing codification, and, by increasing the breadth of context.
First, the less knowledge or technology is codified, the more time and effort potential foreign competitors need to understand, codify, and appropriate it, particularly if these competitors must, in turn, pass on the knowledge to their own personnel. This gives organisations more time to identify the misappropriation behaviour and take suitable actions. Second, the more interrelated people necessary to complete the knowledge-enabled routine are, the more difficult it is for potential competitors to gain access to the entire technology system. In other words, an organisation can increase the breadth of context of its key knowledge by requiring interdependence among people completing the underlying routines or processes.
Knowledge embeddedness and transfer
Organisations need to recognise that knowledge transfer extends beyond the typical explicit form; it also includes in-scope business processes, organisational structures and other context/background information. A key argument is that, through membership in a network and the resulting repeated and enduring exchange relationships, the potential for knowledge acquisition by the network members is created. Informal networks are central in getting work done in an increasingly dynamic and complex business environment. Many retention and transfer approaches focus too heavily on codified knowledge or on an individual's knowledge independent of the network of relationships critical to getting work done. As work has become more complex and interdependent, it is rare for individuals to accomplish anything of substance on their own.
Yet, few knowledge management approaches focus on these network-based assets and, although these networks and relationships are seemingly invisible, a loss would affect the overall knowledge quality and substantially hinder its practical use for value generation. In this context, Social Network Analysis (SNA) can be used as a diagnostic method for collecting and analysing data about patterns of relationships among people, groups, and organisations. Key knowledge vulnerabilities in a network can be identified by virtue of what a person knows and how he or she communicates, as well as by assessing an individual's "informal" prestige and influence. Additional insights can be generated by investigating specific network positions e.g. central connectors, peripheral players, and brokers.
Relational view of knowledge transfer or loss
Several methods can be used to collect the necessary data for the SNA e.g. structured interviews provide a broad spectrum of contextual information, but they are resource intensive, whereas surveys are more efficient in global or distributed settings where questionnaires can be administered using web-based tools. As what you ask, as well as how you do it, significantly affects the subsequent feedback from respondents, based on research done by Steve Borgatti and Rob Cross, Table 1 suggests suitable topics or questions. Stanley Wasserman, professor of sociology, psychology and statistics at Indiana University and chief scientist for Visible Path, a software company devoted to analysing social networks, highlights that, as so many communications are electronic these days, it has become much easier to investigate who is talking to whom. The investigation of E-mail or intranet traffic using sophisticated software packages adds another analytic dimension and enhances the overall quality and reliability of the relational data pool.
Interpretation and related insights
"It is easy to impose a pattern less easy to make it stick less still to discover one there."
Richard Burns in "Building a snowman"
Depending on the specific focus of the investigation the first step usually targets the identification of key players followed by the analysis of important relationships and the subsequent identification of informal groups or clusters. Since a picture really is worth a thousand words, visual analysis of the collected SNA data using graphs plays an important role. If the questionnaire has been designed accordingly, a graph can picture the distribution of knowledge within a given environment.
Referring to Figure 2 a graph can visualise an organisation's or a team's knowledge sharing behaviour, indicating more central as well as more peripheral actors. In addition, the calculation of actor-related indices allows the assessment of an individual's "informal" prestige, influence, and activity e.g. focusing on information or knowledge sharing activities. This exercise supported an Australian telecom company in the identification of imbalances between nicely designed new formal team structures and the informal but highly influential fabric underneath.
Figure 2: Visualisation of knowledge transfer relationships
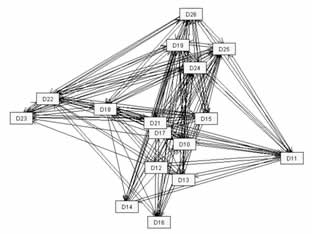
According to research carried out by the Network Roundtable at the University of Virginia unique knowledge is held by three key network roles: central connectors, peripheral players, and brokers. Certainly individual knowledge is important; however, most organisations can replace key expertise if they are willing to spend sufficiently. In contrast, network connections that enable work to get done in a given context is more difficult to replace. The researchers urge that taking a close look at the network roles, and the specific knowledge associated with each, can help organisations identify critical knowledge areas to protect and the potential approaches to start with.
Central connectors are those that have a high number of direct information relationships and possess a strong awareness of expertise in a network, as well as "organisational wisdom". Their deep, network-embedded technical expertise is critical in both day-to-day operations and times of crisis. They are able to perform intuitive judgments and analyse problems from different perspectives. Brokers are those who have ties across subgroups in a network and so have a unique ability to help an organisation capitalise on opportunities requiring the integration of diverse expertise. Brokers often play a key translating function at a technical level, with their knowledge of the expertise and terminology of different groups.
They also play an important translating function at a cultural level by understanding and appreciating differences in values and norms across groups. Research carried out by the author showed that brokerage capabilities are especially important in virtual projects where the project manager has to be able to identify and connect the different social cliques. Peripheral actors have the fewest ties and often reside on the boundaries of a network. Individuals on the periphery tend to be more disengaged and dissatisfied with the organisation or project than those who are well-connected. Nevertheless, peripheral employees often possess important knowledge and expertise and can provide new and innovative perspectives on particular issues. Moreover, findings by the Network Roundtable, suggest that peripheral actors had roughly an equivalent number of relationships outside the organisation as central employees.
Thus, in the light of the investigative aspects mentioned, SNA can support organisations in identifying the informal structure and "real" communication relationships in a multi-stakeholder project or international joint venture. Key knowledge carriers and transfer relationships can be disclosed, potential threats uncovered, and protective actions initiated.
This Article is authored / contributed by ▸ Frank D B. who travels from Duesseldorf, Germany. Frank D is available for Professional Consulting Work both Virtually and In-Person. ▸ Enquire Now.
Comments
What's your opinion?
1 more Articles by Frank D
50













